VIDEO TRANSCRIPTION
Description generated by Skrybot
No description has been generated for this video.
Transcription generated by Skrybot
I'm Sin with the Osin Dojo, and in this video, we're going to talk about Osint. So what exactly is Osint? Perhaps the easiest way to explain this is to break it down into two parts that make it up. Open Source and Intelligence. The open source part of Osint refers to the type of information collected. That is, that this information collected is publicly available. This can include a number of sources, whether online ones like social media profiles, public satellite imagery, or even non-online media such as newspapers, radio broadcasts, and other physical media. Keep in mind that being publicly available doesn't necessarily mean that it's going to be free. Next is the Intelligence portion of Osint.
Quite honestly, this is the concept that most newcomers seem to struggle with the most. You might have heard somebody say, I Osinted them, or I did some Osint on this or that, when they simply mean that they collected information. And so, to be clear, Osint is not just searching for information online, as this in itself is not intelligence. Without intelligence, this is simply open source information. Let's say we're investigating a person of interest. Simply identifying data associated to our person of interest, such as social media accounts, friends, photos, or previous arrest records, would only be open source information.
Now, we can take that data and analyze it to see what places our target frequents, as well as which people they have close and continuing contact with. We could then aggregate the locations from our target social media check-ins, their friends and family's houses, as well as places where they were previously arrested at. We can then utilize this analysis and maybe predict possible routes of travel for our target. As you can see, intelligence is a more formal process. This process typically involves taking collected information, analyzing it, and then turning that into a product which you can then disseminate to stakeholders.
Now that we have a basic understanding of what Osint is and isn't, the next thing we're going to look at is the intelligence cycle. Earlier on, you may have heard me say things like collect, analyze, and disseminate. Those are not just buzzwords, but are in fact critical steps of the intelligence process. Here we have a sample intelligence cycle. Now depending on your agency or company, you may have an intel cycle that slightly varies from this one. I've seen intel cycles with as few as four sections, as well as some with as many as seven.
The first step of the cycle at the top is what we have listed as the preparation phase, though you may also see it commonly labeled as planning and direction. Here is where you will receive your requirements and build your plan on how exactly you will meet those requirements. Following this, we have the collection phase where you begin collecting your raw intelligence. You then move on to the processing phase, taking the data you collected and processing it in preparation for your analysis. The analysis phase is where you begin generating your intelligence from your collected and processed data. This is also commonly referred to as the analysis and production phase, as it's where you begin producing your intelligence product.
Then you have the dissemination phase. Here is where you'll send your findings to stakeholders as a completed intelligence product, such as a report. Once they've had time to review, they may come back with additional questions or related requirements, causing you to enter the preparation phase once again. You may go through many iterations of these steps before you fully satisfy your requirements. I highly recommend you keep a copy of the intelligence cycle handy to reference early on in your career. However, I assure you it will quickly become second nature as you progress as either an analyst or an investigator.
Speaking of analysts and investigators, who uses OSINT in their career? Although those in military, government, and law enforcement tend to be the most common, they aren't the only folks using these techniques. White hat hackers, pen testers, and social engineers may also leverage OSINT prior to engaging with their target. Law firms may also use OSINT in order to gather information about ongoing cases, and financial analysts may leverage OSINT to make investment recommendations. Then there are numerous roles in things like trust and safety, personal and brand protection, anti-piracy, and cyber threat intelligence. One thing to keep in mind is that most jobs are not strictly OSINT only, and will instead require other skill sets and job duties.
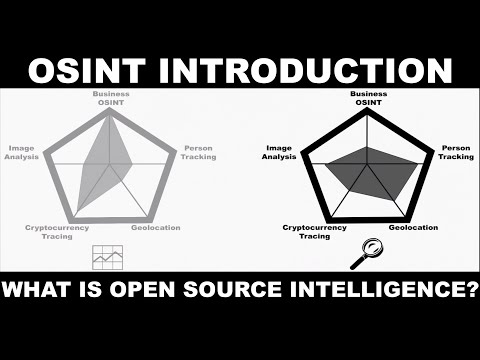
With this in mind, I also want to point out that there are numerous specializations within the realm of OSINT, and no one person will be an expert on everything. Instead, I encourage you to find out what genres of OSINT you enjoy the most and focus on those first. For example, a financial analyst may need more experience in business-related OSINT and tracing cryptocurrency. However, they may not need extensive knowledge of image geolocation or person tracking. Conversely, a general investigator would likely need a core understanding across multiple topics. As you can see, the role or genre of OSINT that you're the most interested in will play a large part into what skill sets you need to strengthen.
Now that you have a general understanding of OSINT, I encourage you to do additional research into different roles and skill sets within the field. As you do so, I recommend you focus on the methodologies, the whys and the hows, and less on the tools. Tools will come and go, but if you understand why or how something works, you're more likely to be able to continue on with an investigation, even if your favorite tool suddenly becomes unavailable. .
S K R Y B O T
Skrybot. 2023, Video transcriptions from YouTube
By visiting or using our website, you agree that our website or the websites of our partners may use cookies to store information for the purpose of delivering better, faster, and more secure services, as well as for marketing purposes.